In the cryptocurrency world, mining is crucial. It validates transactions, and successful miners gain new cryptocurrency for their efforts. However, it uses an enormous amount of energy, so what do miners do? Get other devices to do it for them. Patrick Brusnahan reports
Mining cryptocurrency is not the most popular task. In July 2018, US congressman Brad Sherman actually called for a blanket ban on buying and mining cryptocurrency.
Both Apple and Google have banned cryptocurrency mining apps from their app stores, in an attempt to stop users having their phones used for that purpose without their knowledge.
Even charities are getting into the game: Unicef recently asked gamers to use their GPUs to help mine cryptocurrency for Syrian refugees. There is also the environmental impact of mining cryptocurrencies such as Bitcoin.
According to the Bitcoin Energy Consumption Index, Bitcoin uses around 32TW of energy every year, enough to power around 3 million US households. In comparison, all Visa transactions in a year only use the energy of 50,000 homes. While most mining efforts are intentional, others are using more illicit forms.
Illicit mining
As cryptocurrency values rise, cybercriminals are using devices such as computers, mobiles, and even smart fridges to illicitly mine cryptocurrency.
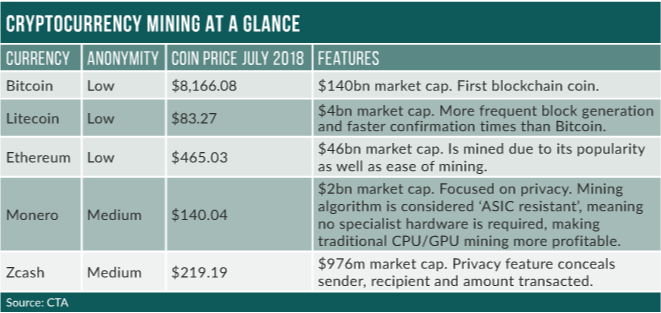
According to the Cyber Threat Alliance (CTA), illicit cryptocurrency mining grew by 459% between 2017 and 2018, and is showing no signs of slowing. Mining malware affected 13% of all Fortinet customer companies in the fourth quarter of 2017, rising to 28% by the first quarter of 2018.
In May 2018, Check Point’s Global Threat Index identified that the CoinHive browser-based miner was having an impact on 22% of its corporate customers. Furthermore, the Palo Alto Networks found approximately 470,000 unique binary-based samples that have the goal of cryptocurrency mining.
Security firm McAfee did not have anything better to add, stating that there was a 629% increase in coin-mining malware in the first quarter of 2018.
In its The Illicit Cryptocurrency Mining Threat report, the CTA says: “While the theft of computing cycles to make money may sound relatively benign in the face of other kinds of cyberincident that can encrypt your data for ransom, steal your intellectual property, or disrupt important functions of critical infrastructure, it is a threat that cybersecurity providers and network defenders must address together to improve our overall cybersecurity.”
A multitude of problems can come from this. On a basic level, it drains resources, causes higher electricity bills, and decreases the productivity of devices and workforces. Cyberattackers are now targeting lessobvious devices to mine: smart TVs, cable boxes, internet set-top boxes and all IoT devices are under threat. On a more serious note, it proves that a device or system has serious cybersecurity flaws. It is also a sign that there may be far larger security problems ahead.
The report continues: “Illicit mining shows no signs of being just a phase for threat actors, but will likely be a continuous and nearly effortless approach to revenue generation. As enterprises experiment with the use of blockchain technologies to conduct business operations, illicit mining outside of cryptocurrencies may itself become a disruptive risk that enterprises must mitigate.” The CTA has specified five reasons for the increase in the activity:
- The increasing value of cryptocurrencies are making the act more profitable;
- Introducing cryptocurrencies for mining via standard devices, such as Monero and Ethereum, provide higher levels of anonymity and a wider attack surface;
- Ease of use;
- Increasing availability of pool mining, where groups of computers band together to mine and increase scale, and
- Enterprises and individuals with lacking security practices and cyberhygiene are bigger targets and often unaware that their operations are being utilised.
The report concludes: “Network defenders have a real opportunity to disrupt threat actors that rely on illicit mining operations to generate revenue. Revenue generation on a per-infection basis is currently low.
“Thus, proper improvements in security may actually drive malicious actors to abandon mining altogether. Even better, making these basic improvements will also increase your defences against other malicious actors that seek to steal or manipulate data or disrupt business processes.”