Since 13 January, 2024, the Egress Threat Intelligence team has seen a steep rise in the number of fraudulent payment attacks using Venmo. By hacking existing or setting up new Venmo accounts, cybercriminals are using legitimate Venmo communications to trick users into approving fraudulent payments.
Masked as annual or monthly subscription payments to brands such as Apple and Amazon, automated emails are sent through the Venmo communications systems with personalised subject lines and payment amounts. These emails contain no malicious links or attachments, and they pass standard email authentication protocols and get through Microsoft 365’s and secure email gateways’ (SEG) defences. The lowest payment value we detected was $97.80 and the highest was $300.
Quick attack summary
- Vector and type: Email phishing
- Techniques: Social engineering, brand impersonation
- Payload: Link-based payment fraud
- Targets: Organisations in North America
- Platform: Microsoft 365
- Bypassed SEG and native security: Yes
The attackers have gained access to or created new Venmo accounts to send personalised email payment requests to other Venmo users. As these emails are sent through the official email system to other Venmo users, the targets are likely familiar with the emails’ design and sender address, as well as the household brand names impersonated in the fraudulent subscription charge requests. This can increase targets’ susceptibility to the attacks, as they blend in with existing communications.
Previously, our team has seen similar attacks using the PayPal platform. In these, cybercriminals warned the target of a potentially fraudulent payment, however if the target clicked on the button in the email, it would authorise the payment rather than cancel it.
What the Venmo phishing attacks look like
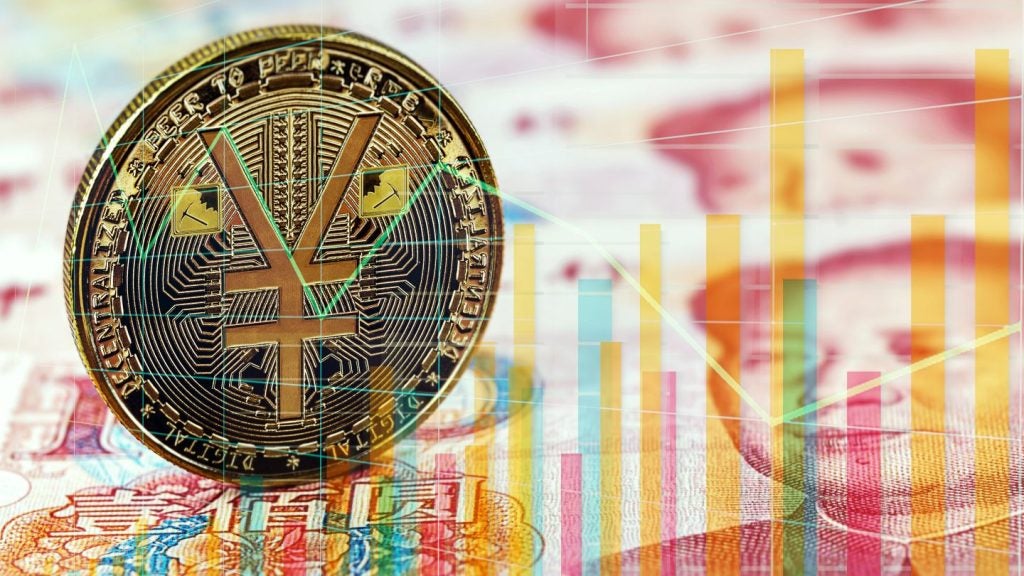
As these emails are sent from an authentic Venmo account, the design and origin domain are legitimate, and the email contains Venmo’s logo and other branding elements (for example, legal verbiage in the email footer and link to unsubscribe). The users receiving these emails are Venmo account holders and will likely have received similar emails from Venmo previously. The consistency in design, sender address, and domain across legitimate and fraudulent request emails is intended to socially engineer victims into believing the attacks are legitimate communications.
US Tariffs are shifting - will you react or anticipate?
Don’t let policy changes catch you off guard. Stay proactive with real-time data and expert analysis.
By GlobalDataThe cybercriminals quote brand names like Apple, Amazon Prime, Norton Security, and AT&T in the subject line and message body with the hopes that the target will not notice the discrepancies in the name of the profile requesting payment and the other details included in the email text, and simply approve the payment by clicking on the hyperlinked button. Again, this is intended to socially engineer the target, who may be deceived into trusting the impersonated brand’s reputation and potentially believe they owe payment for a subscription.
The emails in this phishing campaign also contain a toll-free contact number that has now received negative reviews online. As the number is toll-free, it cannot be traced back to the attackers. Including a contact number is another example of social engineering being used to reassure targets of the authenticity of the request.
Should the target call the toll-free number included in the email, the attackers would likely encourage them to pay the request and divulge even more information, which could be used to defraud them further.
As these emails originate from Venmo itself, usually sent from ‘venmo@venmo.com’, they pass email authentication protocols like SPF, DKIM, and DMARC. In addition, because they don’t contain a known malware payload or hyperlink to a known phishing website, they also get through Microsoft 365’s and secure email gateways’ detection.

Egress analysis: ‘Hijacking’ the Venmo platform, a multi-channel attack, and subscription brand impersonation
‘Hijacking’ the Venmo platform
By using the legitimate Venmo system, cybercriminals ensure that their payment requests pass email authentication procedures and emails get through the traditional signature-based and reputation-based detection used by Microsoft 365 and SEGs. Instead, textual analysis of the email body is required to reliably detect that it contains a fraudulent request.
Additionally, the cybercriminals also intend to ‘hide’ their requests among legitimate communications sent via the Venmo platform. The targets are already Venmo users, so they will be familiar with the format and style of the automated emails, which can lead to complacency. People have a tendency to click first and think later when their suspicions are lower.
A multi-channel attack using a toll-free contact number
Phone numbers included in phishing emails are usually authentic and added to lend credibility to the attack (should, for example, the target search the number online to verify an email’s legitimacy). Instead, in this Venmo campaign, the attackers set up a toll-free number and requested that targets call that number if there was an issue.
The number was included in the personalisation box of the Venmo email template, which means the attackers can swap numbers in and out: once a particular number has been flagged too many times as malicious, they can simply replace it with a new number and launch the second part of their attack all over again.
Speaking to targets over the phone creates a second channel for this attack, providing cybercriminals with the opportunity to convince them to complete the fraudulent payment request, as well as obtain other information that could be used for future fraud attempts or other attacks.
Subscription brand impersonation
By leveraging well-known brand names like Apple, Amazon Prime, and Norton, the attackers attempt to make their emails appear as authentic as possible. According to our cyber analysts, the lowest payment amount requested in the Venmo campaign is $97.80 and the highest was $300. Our experts commented that the value of the payment requested is kept moderately low to avoid suspicion.
As there is no way for the attackers to know specifically whether each of their targets uses the service quoted in the email, choosing to mention a global brand increases the probability of some of their emails reaching actual customers.
In the email screenshots above, we can see that Norton and Apple are the brands mentioned but note that the attackers cannot change the name of the person making the payment request. It’s human nature that the focus of the email could be the price, especially when the email is coming from a company like Venmo.
If the target is doing a risk check, seeing a brand that they pay on either a monthly or an annual basis might just tip the scales for them, and instead of discarding the email altogether, they quickly click through.
Staying protected from targeted phishing emails
As they’re sent using a legitimate platform and don’t contain a ‘traditional’ payload (malware or hyperlink to a phishing website), these attacks get through Microsoft 365’s and SEG defences. And warning users to look out for the ‘typical’ signs of phishing won’t work: hovering over the hyperlink will show a legitimate Venmo URL, the email is sent from a known and trusted address, and it uses Venmo’s legitimate templated branding and wording. This means that targets would need to spot either the mismatch between the impersonated brand and Venmo account name, or recognise they’re not due to pay the brand via Venmo at this time.
Consequently, organisations should implement advanced anti-phishing technology that uses AI-powered behavioural based security. In particular, natural language processing (NLP) is used to analyse the content within the email body and can detect phishing attacks that exclusively leverage social engineering and don’t contain a traditional payload. With an ongoing trend of attacks being designed to bypass existing defences and becoming more difficult for targets to identify, organisations need to ensure they layer the right technologies into their environment to detect and prevent the broad spectrum of attacks.
James Dyer is Egress’ Threat Intelligence Lead